 KSET Computer Science Unofficial Answer Key 2025 Available; All sets questions with answers
KSET Computer Science Unofficial Answer Key 2025 Available; All sets questions with answers
KSET Computer Science Unofficial Answer Key 2025
: Candidates can check out KSET Computer Science Unofficial Answer Key 2025 here for Paper 2. The answer key has been provided for all 100 questions. Through the answer key, candidates can evaluate their performance in the test and analyze what scores they are likely to get. For every right answer, candidates will get 2 marks. The full marks of the paper are 200. It is important to note that this is an unofficial answer key, and there might be errors. Until the official answer key is released, candidates can get an idea of their score by referring to the unofficial key below.
Also Read |
KSET Paper 1 Unofficial Answer Key 2025 Available; All sets questions with answers
KSET Computer Science Unofficial Answer Key 2025 for Paper 2
Candidates can check out KSET Commerce Science Unofficial Answer Key 2025 below, along with the questions for Paper 2:
Question Number | Questions | Answers |
|---|---|---|
1 | Arrange the component-based development process activities in the correct order: a. Requirement analysis b. Component qualification c. System design with reuse d. Component adaptation e. Component composition f. Component discovery g. System integration and testing (1) f, a, b, c, d, g, c (2) a, c, f, b, d, e, g (3) b, a, f, c, d, e, g (4) a, f, c, b, d, g, e | (2) a, c, f, b, d, e, g |
2 | In a spiral model cycle, the probability of failure for each iteration due to risk is 10%. If there are 4 cycles, then what is the probability that the project completes all cycles without failure? (1) 0.6561 (2) 0.9 (3) 0.3439 (4) 0.9999 | (1) 0.6561 |
3 | Match the Agile practices with their corresponding principles or benefits: a. Pair Programming (i) Avoids integration issues by validating changes frequently in shared repositories. b. Test-driven Development (ii) Ensures correctness through automated specification before implementation. c. Continuous Integration (iii) Facilitates early problem discovery and real-time code review. d. Refractoring (iv) Improves internal code quality, altering external behaviour (1) ai, bil, clii, div (2) ali, bili, civ, di (3) aiv, bi, cii, diii (4)aiii, bii, ci, div | (4) aiii, bii, ci, div |
4 | Given below are two statements. One is labelled as Assertion and the other is labelled as Reason. Assertion (A): High cohesion within a module and low coupling between modules result in increased maintainability and reusability of a software system. Reason (R): High cohesion implies that each module performs multiple unrelated tasks, increasing its independence from other modules. Choose the most appropriate answer from the following options. (1) Both A and R are true, and R is the correct explanation of A (2) Both A and R are true, but R is not the correct explanation of A (3) A is true, but R is false (4) A is false, but R is true | (1) Both A and R are true, and R is the correct explanation of A |
5 | In basic path testing, the number of independent paths through the code is computed using cyclomatie complexity. Which of the following statements is correct regarding cyclomatic complexity? (1) Cyclomatic complexity number of nodes - number of edges + 1. (2) Cyclomatic complexity provides an upper bound on the number of required performance tests, (3) Cyclomatic complexity helps in identifying infeasible test cases for black-box testing. Cyclomatic complexity - E-N+2P, where P is the number of connected components in the control flow graph. | Cyclomatic complexity - E-N+2P, where P is the number of connected components in the control flow graph. |
6 | Given below are two statements. One is labelled as Assertion and the other is labelled is Assertion (A): White-box testing is essential for detecting logic errors that may not be exposed through black-box testing, especially in safety-critical systems such as avionics or medical devices. Reason (R): White-box testing allows analysis of control structures including decision points, loops and internal data flow, ensuring through coverage of execution paths. Choose the most appropriate answer from the options given below: (1) Both A and R are true, and R is the correct explanation of A (2) Both A and R are true, but R is not the correct explanation of A (3) A is true, but R is false (4) A is false, but R is true | (1) Both A and R are true, and R is the correct explanation of A |
7 | Which of the following best describes the purpose of a Time-Line (Gantt) chart in project scheduling? (1) To define critical paths and slack times between tasks (2) To graphically represent task dependencies with nodes and arrows (3) To display resource availability across overlapping activities (4) To map task durations along a horizontal time scale for visual tracking | (4) To map task durations along a horizontal time scale for visual tracking |
8 | Which of the following best captures the distinction between change control and version control in software configuration management? (1) Change control handles concurrent file updates, version control manages customer requirement changes. (2) Change control deals with evaluating and approving changes, version control maintains the history and integrity of source artifacts. (3) Change control is applied only during testing, version control is applied during development. (4) Change control eliminates the needs, version control is applied in agile environments. | (2) Change control deals with evaluating and approving changes, version control maintains the history and integrity of source artifacts. |
9 | In object-oriented design, what is the primary purpose of information hiding? (1) Increase execution speed by avoiding modularization. (2) Prevent subclassing and inheritance. (3) Limit the exposure of internal module details to reduce system complexity and error propagation. (4) Allow direct modification of all class members by other objects. | (3) Limit the exposure of internal module details to reduce system complexity and error propagation. |
10 | Assume a software team applies COCOMO II Early Design Model. If the system is later migrated to a cloud-native microservices architecture, then which cost driver becomes the most volatile and error-prone in recalculating effort? (1) Product Complexity (2) Platform Volatility (3) Required Software Reliability (4) Database Size | (2) Platform Volatility |
| 11 |
11. Assume the following priorities in evaluating an expression (1) paranthesis (2) exponentiation (3) division and multiplication (4) addition and subtraction (5) assignment. What is the equivalent post-fix expression of the infix expression ab/c^d (e+1)-g/h.
(1) abcdef+gh-*/- (2)abcd/ef+*gh/-- (3)abcdef+gh/-- (4) abcdef/+*gh-/- | (2)abcd/ef+*gh/-- |
| 12 |
Which one among the following are true about circular queue with queue capacity being n (numbered from 0 ton1), 'f' and 'r' being front and rear pointers to the first, and the last elements?
a. The Queue is full if (r + 1) mod n--f. b. The maximum number of elements that can be stored in a Queue is n-1 c. This is an efficient algorithm compared to linear Queue d. This is a non-linear data structure. (1) a, b and d (2) b, c and d (3) a, b and c (4) a and b | (4) a and b |
| 13 |
Which one of the following are true about Huffman Algorithm?
a. It is Dynamic Programming Algorithm b. It is a Greedy Algorithm c. Used for text compression d. Used for image compression (1) a and c only (2) b and e only (3) a and d only (4) b and d only | (2) b and e only |
| 14 | 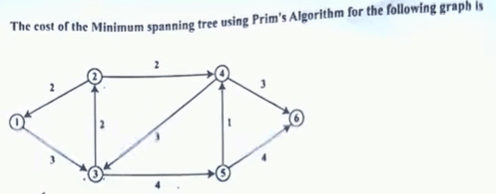 (1) 10 (2) 11 (3) 12 (4) 17 | (1) 10 |
| 15 |
Given the inorder of a tree as e, b, f, c, g, h, d and pre-order of the tree as c, b, e, i, d, g, n, the post-order of the tree is
(1) e, f, b, h, c, g, d (2) e, f, b, h, d, g, c (3) f, e, b, h, g, d, c (4) e, f, b, h, g, d, c | (4) e, f, b, h, g, d, c |
| 16 |
Which one among the following is true about a binary tree?
a. The indegree of the root is zero b. The outdegree of a leaf node is zero c. The maximum number of element a tree with depth d can have is 20-1 d. Is a subset of a graph (1) (a) and (c) are correct, (b) and (d) are false (2) (a), (b) and (d) are correct, (c) is false (3) (a), (b) and (c) are correct, (d) is false (4) (c) and (d) are correct | (3) (a), (b) and (c) are correct, (d) is false |
| 17 |
The complexity of brute force algorithm to find all the substrings in a given string of 'm' characters and a substring of length 'n' (where m>>n) is
(1) 0 (mn) (2) 0 (m) (3) 0 (n) (4) 0 (mn 2 ) | (1) 0 (mn) |
| 18 |
A model which uses the previously computed values for further computation is called
(1) Greedy Algorithm (2) Backtracking (3) Branch and Bound (4) Dynamic Programming | (4) Dynamic Programming |
| 19 |
19. Match the following:
List-1 List-11 a. Prim's algorithm (i) Dynamic Programming b. Queen's problem (ii) Divide and conquer c. Quick sort (iii) Greedy Algorithm d. Binomial coefficient (iv) Backtracking (1) a-iii,b-iv, e-ii, d-i (3) aiii, bii,c-i, d-iv (2) aiii, biv, c-i, d-ii (4) a-iv, b-ii, ci,d-iii | (1) a-iii,b-iv, e-ii, d-i |
| 20 |
In a multiprocessor environment, assume that there are n = 8 elements, and the number of processors given N = 4. If we use the Binary tree model to find the greatest of 'n' elements using parallel processing, then the time taken to find the greatest of 'n' elements is ____ (Assume the communication cost to be 0)
(1) 0 (log 2 n) (2) 0 (log 2 N) (3) 0 (N log 2 , n) (4) 0 (n log 2 , N) | (1) 0 (log 2 n) |
| 21 |
Select the invalid paradox type from the following:
(1) Falsidical (2) Veridical (3) Antinomy (4) Opposidical | (4) Opposidical |
| 22 |
If the languages Land Lare recursive enumerable, then Lis
(1) Regular (2) Context-free (3) Context-sensitive (4) Recursive | (4) Recursive |
| 23 |
A grammar is called ambiguous if
(1) Two or more productions have the same non-terminal on the left-hand side. (2) A derivation has more than one associated sentence (3) A sentence having more than one derivation (4) Productions having mostly terminal symbols | (3) A sentence having more than one derivation |
| 24 |
24. A context-sensitive language is accepted by
(1) Finite automata (2) Linear-bounded automata (3) NFA (4) DFA | (2) Linear-bounded automata |
| 25 |
Problems that can be solved in polynomial time are called
(1) Tractable Problems (2) Intractable Problems (3) Decidable Problems (4) Undecidable Problems | (1) Tractable Problems |
| 26 |
The time complexity of constructing an LP parser is _____, given |n| is the size of the grammar.
(1) 0 (n) (2) 0 (n log n ) (3) 0 (2 |n| ) (4) 0 (n²) | (4) 0 (n²) |
| 27 |
27. The grammar S→ XYZ
Y. val = X. val Y. val = S. val Y. val = Z. val is (1) S-attributed Grammar (2) L-attributed Grammar (3) Neither S-attributed nor L-attributed Grammar (4) Both S-attributed and L-attributed Grammar | (3) Neither S-attributed nor L-attributed Grammar |
| 28 |
Pick the right sequence of abstract machines according to their increasing order of power.
(1) FA→ DPDA→ NDPDA → TM (2) FA→ NDPDA→DPDA → TM (3) FA→ DPDA→ TM → NDPDA (4) TM→ DPDA → NDPDA → FA | (1) FA→ DPDA→ NDPDA → TM |
| 29 |
A symbol table in assembler contains
(1) Mapping of variables and their memory addresses (2) Program code and data (3) Input and output instructions (4) Machine instructions and opcodes. | (1) Mapping of variables and their memory addresses |
| 30 |
Which of the following is not a common type of data flow analysis performed by compilers?
(1) Constant propagation (2) Dead code elimination (3) Live variable analysis (4) Type checking | (4) Type checking |
| 31 |
A system transmits data at 1200 bytes per second using 4 bits per signal limit. What is the baud rate?
(1) 2400 Baud (3) 38400 Baud (2) 9600 Baud (4) 4800 Baud | (1) 2400 Baud |
| 32 |
____ is a digital modulation technique where the amplitude of a carrier wave is varied in accordance with the digital data being transferred, while frequency and phase remain constant.
(1) Amplitude shift keying (2) Phase shift keying (3) Frequency shift keying (4) Quadrature amplitude modulation | (1) Amplitude shift keying |
| 33 |
The bandwidth of a noisy channel is 3000 Hz and whose signal to noise ratio is 3162. What will be the maximum data rate of the channel?
(1) 37524 bps (2) 36523 bps (3) 35922 bps (4) 34890 bps | (2) 36523 bps |
| 34 |
A transmission uses CRC for error detection, the message is 1101011011 and the generator polynomial is G (x) = x + x + 1. What will be appended at the end of the message?
(1) 1111 (2) 1110 (3) 1101 (4)1100 | (1) 1111 |
| 35 |
35. In a mesh topology with 100 devices, the number of physical connections required is ___
(1) 9900 (2) 4950 (3) 200 (4) 9801 | (2) 4950 |
| 36 |
If a file is encrypted and then transmitted over a network using TCP/IP, then which layer handles the encryption and which handles retransmission if the file is lost?
(1) Application layer - Transport layer (2) Presentation layer - Data link layer (3) Session layer - Network layer (4) Transport layer - Application layer | (1) Application layer - Transport layer |
| 37 |
37. Match the following:
IP Address 1. 0.0.0.0 ii. 127.255.255.255 iii. 192.0.2.0/24 Ιν. 224.0.0.1 Uses for (a) Documentation/examples (RFC 5737) (b) Multicast address for all hosts on a subnet (c) Unknown or default route address (d) Local host loopback testing (1) i-c, ii-d, iii-a, iv-b (2) i-d, ii-a, iii-b, iv-c (3) i-b, ii-c, iii-a, iv-d (4) i-b, ii-a, iii-d, iv-c | (1) i-c, ii-d, iii-a, iv-b |
| 38 |
In a columnar transposition cipher, the key is "LARGE". What will be the cipher text for the plain text "COMPUTERSCIENCE" (without space) using a simple columnar transposition?
(1) CTIOEEMRNPSCUCE (2) MRNCTIPSCUCEOEE (3) OEEUCEPSCCTIMRN (4) CETMPOIRECUSENC | (2) MRNCTIPSCUCEOEE |
| 39 |
In the RSA algorithm, let NPxQ33, and let the decryption key D-7. If the ciphertext corresponds to the letter "E", determine the original plaintext letter.
(Assume A1, B2, Z=26). (1) S (3) N (2) U (4) E | (2) U |
| 40 |
Five channels, each with a 100 kHz bandwidth are to be multiplexed together. What is the minimum bandwidth of the link if there is a need for a guard hand of 10 kHz between the channels to prevent interference?
(1) 500 kHz (2) 540 kHz (3) 550 kHz (4) 100 kHz | (2) 540 kHz |
| 41 |
Determine which machine (M) passes the 'Turing Test', if it is subjected to 'imitation game conducted in 'Controlled Environment'.
(1) M performs calculations quickly (2) M generates random responses (3) M identifies emotional intelligence (4) M engages in conversation without identified as non-human | (4) M engages in conversation without identified as non-human |
| 42 |
42. Match the following 'Heuristic Search' with respect to "Hill climbing" Algorithm:
List-I a. Steepest Ascent Hill Climbing b. Hill Climbing Algorithm c. Plateau d. Ridge List-II (i) Variant of "Generate and Test algorithm" (ii) Gradient search (iii) Area higher than surrounding (iv) Flat area of the search space (1) a-ii, b-i,c-iv, d-iii (2) ai, biv, c-iii, d-ii (3) ai, bil, c-iii, d-iv (4) a-iv, b-iii, c-ii, d-i | (1) a-ii, b-i,c-iv, d-iii |
| 43 |
Relate the Al methodologies of knowledge representation in right match.
List-1 a. NLP b. Representation in structured network c. Classes in ontology d. Expert system (i) Inference engine (ii) Abstract categories of related topics/concepts (iii) Semantic network (iv) Semantic analysis (1) a-iv, b-iii, e-ii, d-i (2) a-iv, b-ii, c-iii, d-i (3) a-iii, b-iv, c-ii, d-i (4) a-i, b-ii, c-iii, d-iv 45. Match the following List-I with List-II: List-I a. Fuzzy system b. Expert system List-11 (1) Decision tree (ii) Inversion Visit Abu Dhabi Sponsored visitabudhabi.ae 8/20 | (2) a-iv, b-ii, c-iii, d-i |
| 44 |
If f(x) = x is my friend, and P (x) = x is perfect, then the correct logical translation of the statem "Some of my friends are not perfect" is _____.
(1) ∀x (f(x)-P(x)) (2) x (f(x)^-P(x)) (3) -(f(x) - P(x)) (4) 3x (f(x)^-P(x)) | (2) x (f(x)^-P(x)) |
| 45 |
Match the following List-I with List-II:
List-I List-II a. Fuzzy system b. Expert system c. Genetic algorithm operator d. Supervised technique (i) Decision tree (ii) Inversion (iii) Inference engine (iv) Dendral (1) a-iv, bi,c-iii, d-ii (2) a-i, b-iv, c-ii, d-iii (3) a-iii, b-iv, c-ii, d-i (4) a-ii, b-iii, c-i, d-iv | (3) a-iii, b-iv, c-ii, d-i |
| 46 |
Given two Fuzzysets A and B with membership function µA (x) = (0.6, 0.5, 0.1, 0.7, 0.8).
μΒ (x) = 10.9, 0.2, 0.6, 0.8, 0.5). Now calculate the value of µ (AB)' (x). (1) (0.1, 0.5, 0.4, 0.2, 0.3) (2) (0.1, 0.5, 0.4, 0.2, 0.2) (3) (0.1, 0.5, 0.4, 0.3, 0.2) (4) (0.1, 0.5, 0.4, 0.3, 0.3) | (3) (0.1, 0.5, 0.4, 0.3, 0.2) |
| 47 |
Let the population of chromosomes in Genetic Algorithm is represented in terms of binary number.
The strength of fitness of a chromosome in decimal form, x, is given by (x) J Sf (x) = where f (x) = x² Σf(x) And the population is given by P where P= {(01101), (11000), (01000), (10011)) Calculate the strength of fitness of chromosome (11000). (1) 49.2% (2) 576.8% (3) 15.10% (4) 14.4% | (1) 49.2% |
| 48 |
Given a "feed forward" ANN with 'n' inputs, 'h' hidden units and 'm' outputs.
Compute how many trainable parameters (weights) are present in ANN, assuming there are no biases. (1) n + m x h (2) n + h + m (3) (n x h) + (h x m) (4) n x h x m | (3) (n x h) + (h x m) |
| 49 |
Match the following and choose the correct option:
Selection method i. Rank selection ii. Tournament selection iii. Roulette wheel iv. Elitism Noise level (a) Higher Noise (b) Lower Noise (c) No Noise (d) Moderate to High (1) i-c, ii-a, iii-b, iv-d (2) i-b, ii-d, iii-a, iv-c (3) i-a, iib, iii-c, iv-d (4) i-d, iic, iii-b, iv-a | (2) i-b, ii-d, iii-a, iv-c |
| 50 |
The back propagation algorithm calculates the gradient of the 'Loss function' with respect to each weight in the network by which of the following mathematical techniques?
(1) Lagrange multiplier (2) Gradient descent (3) K means algorithm (4) Chain rule of calculus | (4) Chain rule of calculus |
| 51 |
Given (P∨Q)
∧
(P∨Q), which of the following mathematical logies is considered as equivalent?
(1) Q (2) P ∧ Q (3) P (4)-Q | (3) P |
| 52 |
Match the following terms with their definitions:
a. Well-ordered Set (i) A set where every pair of elements are comparable b. Partial-ordered Set (ii) Every non-empty subset has a least element c. Totally-ordered Set (iii) A set where every pair of elements not necessarily to he comparable d. Empty Set (iv) A set with no elements (1) aii, bili, c-i, d-iv (2)aii, bi, e-iii, d-iv (3) aii, biii, e-iv, d-i (4) aiv, biii, c-ii, d-i | (1) aii, bili, c-i, d-iv |
| 53 |
. Given U = \{1, 2, 3, 4, 5, 6, 7, 8, 9, 10\} Let A = \{1, 2, 3, 4, 5\} B = \{1, 2, 4, 8\} C = \{1, 2, 3, 5, 7\} and D = \{2, 4, 6, 8\} Determine (AB)-(COD).
(1) (1, 3, 5, 7, 9, 10) (2) (1, 3, 4, 5, 6, 7, 8, 9, 10) (3) (1, 2, 3, 4, 5, 8) (4) (1, 3, 4, 5, 8) | (4) (1, 3, 4, 5, 8) |
| 54 |
What is the probability of an odd sum when two dice are rolled?
(1) 12/36 (2) 18/36 (3) 24/36 (4) 9/12 | (2) 18/36 |
| 55 |
A party of n persons sit at a round table, find the odd against two specific individuals sitting next to each other.
(1) (n-3):2 (2) (n-3):8 (3) (n + 3) / 4 (4) (n + 3) / 16 | (1) (n-3):2 |
| 56 |
Consider a connected, undirected graph G-(V, E) where |V|= n and [E=m. Which of the following statements must be true for a spanning tree of G?
a. A spanning tree of G will always have exactly mn+1 edges b. Any subgraph of G with exactly n-1 edges is guaranteed to be a spanning tree c. The number of spanning trees in G can be computed using Kirchhoff's matrix tree theorem d. A spanning tree of G is always unique for any given graph (1) (b) and (d) are correct (2) only (c) is correct (3) only (a) is correct (4) (a) and (d) are correct | (2) only (c) is correct |
| 57 |
Let G be a group defined by a b = (ab/2); where the elements of G are nonzero real numbers. The solution of 3*x4 is given by
(1) 8/3 (3)-3/8 (2)-4/5 (4) 4/3 | (2)-4/5 |
| 58 | 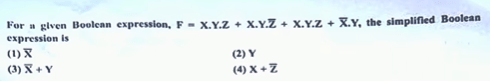 | (2) Y |
| 59 |
Consider a weighted complete graph G on of the vertex set (V
1
, V
2
, V
3
, V
4
, .... V
5
) is 2 11-J such that the weight of the edge (V
1
, V
j
) is 2 | i - j |. The weight of minimum spanning tree of G is
(1) n 2 -1 (2) n²/2 (3)2n-2 (4) n² | (2) n²/2 |
| 60 | 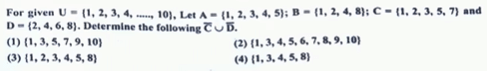 | (1) {1, 3, 5, 7, 9, 10} |
| 61 |
The decimal equivalent of the hexadecimal number F3E is
(1) 8530 (2) 8544 (3) 3902 (4) 3888 | (3) 3902 |
| 62 |
Match the following:
List-1 List-II a. MAR b. MBR c. IR d. PC (i) Holds the address of the next instruction to fetch (ii) Holds the instruction for decoding (iii) Holds the address of instruction or data (iv) Holds the data (1) a-iii, b-iv, e-i, d-ii (2) a-iv, b-iii, c-i, d-ii (3) a-iii, b-iv, c-ii, d-i (4) a-iv, b-iii, c-ii, d-1 | (3) a-iii, b-iv, c-ii, d-i |
| 63 |
"Sequential portion of the program does not change with respect to machine size, however, the parallel portion is evenly executed by 'n' processors results in a reduced time" is
(1) Moore's Law (2) Flynn's Law (3) Banker's Law (4) Amdahl's Law | (4) Amdahl's Law |
| 64 |
The first machine cycle of an instruction is always a
(1) Memory read (2) Fetch (3) I/O read (4) Memory write | (2) Fetch |
| 65 |
If the operand is given explicitely in the instruction, the addresing mode is called
(1) Immediate (2) Absolute (3) Direct (4) Indirect | (1) Immediate |
| 66 |
Consider cache with 128 blocks of 16 words, and main memory has 4096 blocks of 16 words, and assume 6-4 sets for the Set Associate Mapping. Match the addressing scheme for cache memory mapping:
a. Direct mapping b. Associate mapping c. Set associate mapping (i) 12 bit for tag and 4 bit for word (ii) 6 bit for tag, 6 bit for set and 4 bit for word (iii) 5 bit for tag, 7 bit for block and 4 bit for word (1) a→i, b→ii, c→iii (2) a→iii, b→ii, c→i (3) a→ii, b→iii, c→i (4) a→iii, b→i, c→ii | (1) a→i, b→ii, c→iii |
| 67 |
Match the following:
List-1 a. Temporal locality of reference b. Spatial locality of reference c. Sequential locality of reference (i) If an instruction is executed now, more likely the instruction will be executed in future (ii) Instructions are executed one after the other (iii) If a group of instructions referred now, more likely that group of instructions will be referred in future (1) a-i,b-iii,c-ii (2)a-iii, b-i, c-ii (3) a-ii, b-iii, c-i (4)a-ii, b-i,e-iii | (3) a-ii, b-iii, c-i |
| 68 |
Match the following:
List-1 a. DRAM List-11 (i) Offloads data transfer main memory to devices bypassing CPU b. DMA (ii) Dynamic memory c. Associative mapping (iii) I/O devices treated as memory locations d. Memory-mapped I/O (iv) Flexible cache mapping by content (1) ai, bii, cili, div (2) 3a-il,b-i,c-iv, d-iii (3) aiii, biv, c-il, d-i (4) aiv, biii, c-i, d-il | (2) 3a-il,b-i,c-iv, d-iii |
| 69 |
In the absence of data and control hazards, the k-unit instruction unit pipeline with n instructions has speed up
(1) (nk/(k+(n-1)) (2) (k+(n-1))/nk (3) nk/((k-1)*n) (4) k+n/(nk) | (1) (nk/(k+(n-1)) |
| 70 |
Consider the following statements regarding the Interconnection topology.
i. In star topology. If the master node is dead, the other nodes (processor) can still interact with each other. ii. In bus topology, only two processors can Interact with each other at any one given point in time. iii. In hyper cube topology, two nodes are connected if there is change in two bits in their processor Identity (processor id) (1) (i) is true. (ii) and (iii) are false (2) (i) and (ii) are true, (iii) is false (3) (ii) is true, (i) and (iii) are false (4) (i) and (iii) are true, (ii) is false | (2) (i) and (ii) are true, (iii) is false |
| 71 |
Match the following:
File Extension a. wav b. .pdf c. .ped d. .WMV File Format (i) structured (ii) image (iii) video (iv) audio (1) a-iv, b-i, c-ii, d-iii (2)aiii, bii, c-i,d-iv (3) a-iii, b-i,c-ii, d-iv (4)a-ii, b-i, civ, d-iii | (1) a-iv, b-1, c-ii, d-iii |
| 72 | 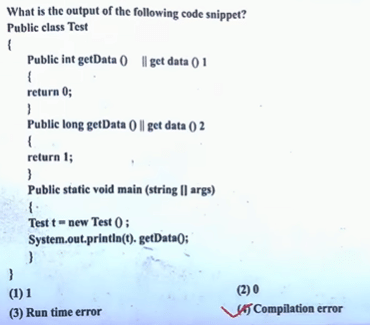 | (4) Compilation Error |
| 73 |
What is the role of linker in compilation?
(1) Translates source code to object code (2) Generates intermediate code (3) Combines different compiled modules (4) Performs code optimization | (2) Generates intermediate code |
| 74 | What will be the output of the following code snippet? | (1) 5 |
| 75 | What is the output of the following program? | (1) Compiler Error |
| 76 | What is the output of the following code? | (2) 2, 20 |
| 77 | A 16 x 16 array having only black and white pixels could be represented by ____. | (3) 96 Bytes |
| 78 | Which of the following matrix represents a 2D rotation by an angle θ? | Option 4 |
| 79 | How much memory is required to implement a z-buffer for a 512 x 512 image with 24-bit depth? | (1) 1 MB |
| 80 | Given 3D-triangle with co-ordinate points A(3, 4, 1), B(6, 4, 2), and C(5, 6, 3). Apply the reflection on the XY plane and find out new co-ordinates of the object. | (3) A(-3, 4, 1), B(-6, 4, 2), and C (-5, 6, 3) |
| 81 |
Identify the correctness of the following statements?
i. Logical data independence is the ability to modify the logical schema without transforming the application programs ii. Logical data independence modifies the logical schema as well as the application programs iii. Logical data independence is complicated to achieve than the physical data independence | (4) (i) and (ii) are incorrect and (iii) is correct |
| 82 |
Identify the correctness of the following statements:
i. The project operation is a unary operation which extracts attributes from a relation ii. The project operation allows us to locate tuples that are in one relation but not in another relation iii. The project operation connects the data across the relations | (1) (i) and (ii) are incorrect and (iii) is correct |
| 83 |
Consider the following statements:
i. Stored procedures can be used to process multiple databases ii. Extended stored procedures are compiled as dynamic link library files iii. Local stored procedures are stored on user-built databases | (2) (i) is correct, (ii) and (iii) are incorrect |
| 84 | _____ eliminates relations between candidate boys. | (4) Boycee-Codd Normal Foam |
| 85 | In _____, whenever a new update is made, multiple versions of the data items are produced | (3) Shadow Paging |
| 86 |
Match the following:
List-1 a. BCNF iff b. 5 NF iff c. 1 NF iff d. 4 NF iff (i) every JD is implied by the candidate keys (ii) every MVD is implied by the candidate keys (iii) all underlying domains contain scalar values only (iv) every FD is implied by the candidate keys | (3) a-iv, b-i, c-iii, d-ii |
| 87 |
Match the following:
List-1 a. Data warehouse b. Data mining c. OLAP d. Aggregation (i) which allows users to analyse data from multiple database systems at once (ii) is the summarization of fact related data (iii) central repository of information that can be analyzed to make more informed decisions (iv) is a process used to discover patterns and relationships in | (3) a-iii, b-iv, c-ii, d-i |
| 88 | Which of the following refers to the problem of finding abstracted patterns (structures) in the unlabelled data? | (2) Unsupervised Learning |
| 89 | Match the following... | (3) a-iii, b-iv, c-i, d-ii |
| 90 | Given the following entries on the table... | (3) gives sum of population of S and N separetely |
| 91 | In the process of macro expansion given... | (4) S 1 is true, and S 2 is false |
| 92 |
Consider a single processor system with four processes A, B, C and D represented as given below, where for each process the first value is its arrival time and second value is its CPU burst time A(0, 10), B(2, 6), C(4, 3) and D(6, 7)
20 Which of the following options gives the average waiting time when preemptive Shortest Remaining Time First (SRTF) and the Non-Preemptive Shortest Job First (NP-SJF) CPU scheduling algorithms are applied to the process? (1) SRTF 6 NP-SJF-7 (3) SRTF-7 NP-SJF-7.5 (2) SRTF-6 NP-SJF-7.5 | (2) SRTF = 6, NP-SJF=7.5 |
| 93 | Match the following... | (2) a-ii, b-i, c-iii, d-iv |
| 94 |
In a system using paging with Translation Lookaside Buffer (TLB), what will be the Effective Memory Access Time (EMAT), if the memory access time is 100 ns, TLB access time is 20 ns, and the TLB hit ratio is 80%?
Assume TLB hit requires one memory access and TLB miss requires two. | (3) 140 ns |
| 95 | Match the following with respect to various memory management... | (4) a-ii, b-iii, c-iv, d-i |
| 96 | Which of the following is not correct about the virtual memory management? | (4) It provides lower degree of programming |
| 97 | Match the following... | (3) i-c, ii-d, iii-b, iv-c |
| 98 | Match the following... | (4) i-c, ii-d, iii-a, iv-b |
| 99 | Which of the following disk scheduling algorithms may result in starvation? | (3) SSTF |
| 100 | Match the following... | (3) i-c, ii-a, iii-d, iv-b |
Keep visiting CollegeDekho for the latest Education News on entrance exams, board exams and admissions. You can also write to us at our email ID news@collegedekho.com.











